In the past couple of years, the number of data breaches and data loss incidents has increased exponentially. According to the Bleeping Computer report, there were over 12 thousand confirmed data breaches in 2018, a staggering 424% increase from 2017.
Most of the breaches involved exposure of user’s personal data and disclosure of business-related documents.
Data breaches and data loss are natural things when you have many people working with information in numerous data analytics, data mining, machine learning operations, accounting, customer support, etc. The tool that avoids this from happening is data loss prevention software.
In this article, we will explain what is data loss prevention, and how to prevent data leakage.
What is Data Loss Prevention (DLP)?
Definition of Data Loss Prevention (aka DLP) is a set of policies and software applications. Its goal is to monitor the information in the system and prevent the possibility of losing or breaching data for various reasons.
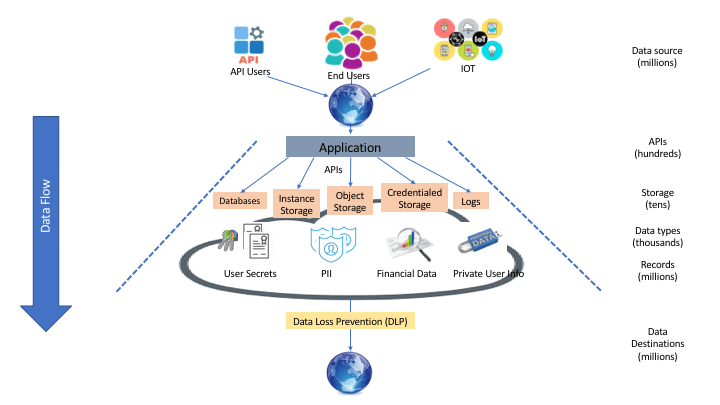
Image source: ShiftLeft Blog
There are three types of data that require special handling:
- Intellectual Property – source code, design documents, process documentation;
- Corporate Data – legal and financial documents, strategic planning documents, employee information
- Customer Data – personal data like name, address, phone number, location, preferences, social security numbers, credit cards, medical records, financial statements, and so on.
Read also: Importance of Data Security & Privacy
Overall, the main focus of DLP (data loss prevention) software is:
- Keeping data safe in use, in motion, and at rest
- Monitoring endpoint data movement
- Vulnerability prevention, i.e., the disclosure of sensitive information (either intentionally or by accident)
Besides, data leakage prevention software helps to identify the source of the insider’s leak in the event of the data breach.
- Providing security measures and fixing weak points in the data processing pipeline – i.e., providing encryption for sensitive data and performing routine backups.
How does Data Loss Prevention software work?
A DLP solution is all about identifying sensitive data, managing its access, and taking measures in keeping it safe.
Data leak prevention revolves around monitoring and analysis tools:
- determine whether a particular data operation is legitimate or threatening to the company’s assets;
- take proper measures to keep data secure.
Data loss protection operation revolves around two concepts:
- Content awareness – the information and its role in business operation;
- Contextual analysis – i.e., the medium of the content and its internal presentation coupled with the intentions of using data;
Action-wise, data loss prevention practices revolve around the following methodologies:
- Encryption – used for basic safeguarding of sensitive data in storage and transit;
- Cryptographic hashing – used for anonymization of personally identifiable data;
- Data fingerprinting to identify and track data in the system (usually for reading, hashing, and storing activities);
- Routine backups of information – used to keep versions of sensitive data intact, especially in cases of unauthorized or accidental changes, movement, or erasure.
Data leak protection software’s modus operandi is broken down into four key components:
- Above every type of data-related operation stands the system’s policy. It defines what kind of data is sensitive and what users can do with it. Most importantly, the policy describes the course of action regarding data loss protection (for example, encrypting sensitive data or sending a notification to admin).
- The management component is an interface for the system’s policy. It is an initial set of regulations to keep things in check. It includes monitoring:
- what data is currently used and its state of access;
- who is using which information;
- where the data is going in the process.
- The identification component uses the system’s policy to find sensitive data and assess its state in the system. It is also used to identify the user and his level of access.
- The protection component is the one that takes action. It is a set of DLP tools designed to safeguard sensitive information from unauthorized access and prevents its loss via the creation of backups. Usually, it is either reporting on something or providing different levels of access and encryption to the sensitive data.
Types of Data Loss Prevention software
There are three major types of Data Loss Prevention software. It is important to note that these DLP tools are used interchangeably for various purposes.
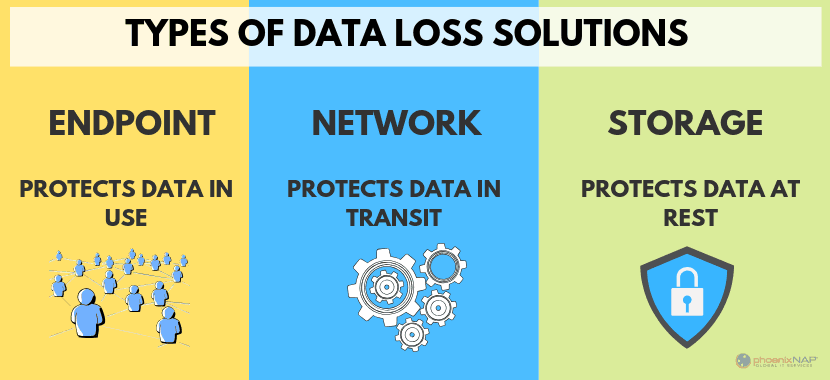
Image source: phoenixNAP
- Network DLP – the type of DLP software where the solution integrates with all of the data points of the Network. This type of DLP is commonly used in corporate networks as a precautionary measure, due to the high volume of various data operations.
- Network DLP monitors the state of data in the Network and keeps an extensive log on its movement and transformations. In a way, it is a kind of fail-safe option that avoids both routine chances of data loss and diligent malice.
- Storage DLP – this type of data loss prevention program is for data lakes on cloud storage. Its primary focus is on keeping the confidentiality and safety of data in the data warehouse.
- The process includes monitoring the sensitive data in the storage and managing its access configuration accordingly. In a way, it is a kind of surveillance service with an alarm.
- Endpoint DLP – this type of DLP software monitors data sharing from point to point i.e., device, storage, or account. For example, you are sharing a market research report with a business analyst. This action is documented in the system’s log.
- For example, if you share this document with somebody outside the system, it is automatically blocked, and you need to enable its access outside manually.
- In addition to sharing, endpoint DLP also keeps an eye on clipboards and even physical devices. While physical storage is not as popular now – it is still used here and there. However, physical devices can break, and this may lead to data loss.
- Endpoint DLP is similar to Network DLP. It monitors where the data goes and what happens to it, but unlike Network DLP, it is workstation-based. Thus, it handles only one source of data operations.
3 reasons to use Data Loss Prevention products
The vulnerability of data on cloud storage is a fact of life, and you have to deal with it. Many unfortunate things can happen to it without proper DLP security. For example:
- Unauthorized access data breach;
- Data Loss – i.e., irreversible change, movement or erasure of sensitive information;
- Storage misconfiguration – exposure of confidential data on the outside.
(Just in case, we have an entire article dedicated to that).
With the number of data breaches growing exponentially with each year (by 2021, total damages are estimated to be up to $6 trillion) – it is reasonable to be cautious.
There are three main reasons why the implementation of DLP solutions is critical for moving forward and expanding the business operation.
1. Compliance
Different government standards and regulations broadly cover the requirements for the safety and confidentiality of sensitive data regarding users and business processes (to name a few – GDPR, HIPAA, SOX, PCI DSS).
In one way or another, they regulate the treatment of personally identifiable and other types of sensitive data.
Implementation of a data loss prevention policy is one of the critical steps for compliance. In addition, the regulations map out the extent of control you have over data and give direction for more efficient data management.
Disclosure or loss of confidential data leads to lawsuits, reputation and credibility damages, and, ultimately, loss of revenue.
2. Better treatment of the company’s assets
A company’s assets what keep the engine rolling. Such valuable data requires strict monitoring of who is using and why. A data loss prevention policy covers the treatment of information such as:
- trade secrets;
- strategic proprietary information;
- customer lists and personally identifiable data;
- business strategies.
The loss or breach of this data can cause a lot of problems for the company. Just ask Facebook.
DLP security policy clearly states types of access for sensitive data and describes courses of action, in any case.
3. Data visibility
The foundation of an effective data loss prevention policy is in understanding what kind of sensitive data is in the system, its location, and who is using it for what purposes.
This process involves constant asset audits, which gives a better grasp of your data.
How to create a successful DLP policy: a six-stage guide
1. Identify which data requires protection;
- Evaluate possible risk factors (for example, the risk of a breach through email communication or exploits in the API framework);
- Assess the vulnerability of different assets (for example, customer lists, legal documents, marketing analytics, and so on).
- Select a priority scale for the protection of different types of data – which types represent what risk to the business operation. For example:
- The app user database is an operational asset always in use, and it requires encryption both in transit and storage.
- The competitor’s research data requires specified access and storage encryption.
2. The documentation of the DLP policy should be as thorough as possible. Everything needs to be written down to keep everybody on the same page. Being thorough provides full clarity of the proceedings and enables full compliance with standards.
- Enforce a Data Loss Prevention policy at the organizational level.
- Keep stakeholders and users aware of DLP policy and its importance.
3. Optimize data management and identify what type of data is unnecessary for business operation. If this type of data is not needed, then it should be removed, and thus, the breach or loss is impossible.
4. Establish transparent metrics (more on that later). Things which can measure the effectiveness of a DLP security policy:
- Percentage of false positives during monitoring;
- The number of security incidents;
- Response time to an emergency.
5. Describe the scope of access to each type of user in the system (heads of departments get more access than junior specialists).
6. Automate the procedure with specialized software. The more workflow is automated, the easier it is to control.
- DLP tools like McAfee DLP use machine learning anomaly detection and behavioral analytics to maintain the precision of DLP management.
- Each user group has its own set of behavioral patterns. This layout allows to quickly identify the intent of the particular data operation and neutralize suspicious activity without sustaining any damage.
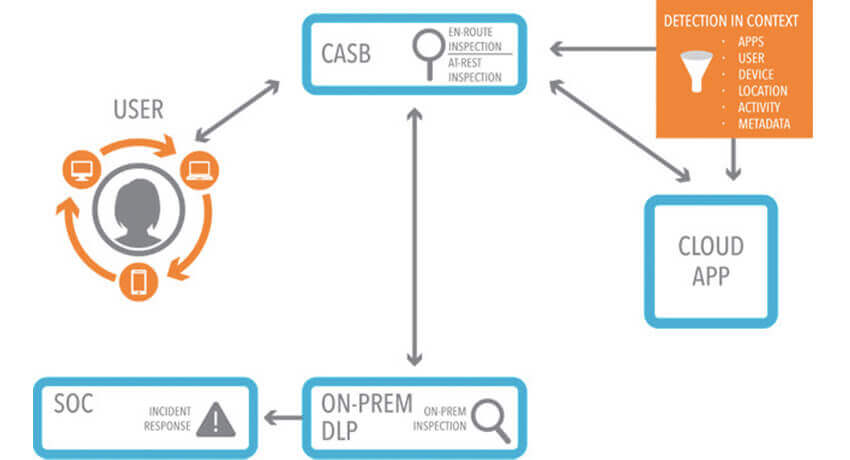
Image source: netskope
6 Metrics to Evaluate the Effectiveness of Data Loss Prevention Practices
Data Loss Prevention is a complex operation with many moving parts. Once implemented, it needs constant optimization and enhancement in order to serve its purpose well.
The best way of keeping data loss prevention tools in shape is to implement tangible metrics of their effectiveness.
Let’s look at them more closely.
1. Data classification success rate
The first step in implementing a Data Loss Prevention solution is data classification. This process identifies and differentiates types of sensitive information and describes its context. It is the backbone of every DLP tool.
Data classification is often performed in a semi-automated mode when the basic groundwork is done by the algorithm and then validated by the operator. The percentage of erroneous classifications can show how much of the sensitive information is left behind by the monitoring tool.
2. Percentage of policy exceptions
A System Data Loss Prevention policy contains a list of the dos and don’ts regarding the use of data throughout the company. It also includes certain types of exceptions from the rules. It can create one-off permission for a specific employee (for example, marketing getting access to project documentation to prepare a case study) or providing wider access to a third party via API (like Facebook for vendors or advertisers).
Monitoring the number of exceptions gives you an understanding of how much of the DLP security policy is really used. It is a good way of optimizing the weak points.
3. Percentage of false positives
Each monitoring system gets its own share of false positives and false negatives. The root of this issue is in the Data Loss Prevention monitoring routines. Some things are less defined or unmentioned, and this causes all sorts of false alarms.
The percentage of such events compared with the number of real alerts is a good measure for the effectiveness of the DLP tool. Helps to identify real data issues.
4. Percentage of fingerprinted databases
Digital fingerprinting is a method of data leakage prevention used to keep an eye on who is using what kind of data for what purpose.
As a metric, it is a good way of understanding the integrity of information and classifying the scope of access.
This helps in identifying tampering and tracing the possible source of a leak.
5. Alert response time
This metric takes into consideration how much time it takes to fix an issue from its emergence to its solution.
It helps to optimize the workflow and figure out the most effective routines of responding to alerts.
How to make your IT project secured?
Download Project Security Checklist
6. State and amount of unmanaged devices
The risk of unmanaged devices is in the lack of control over them. They create uncertainty because you can’t enforce data loss protection policies.
Such devices are data endpoints (employee workstations or smartphones), cloud storage, and removable storage (USB sticks et al.) – basically any departure point for information.
The goal of this metric is to monitor the number, type, and storage size of devices outside the company’s system infrastructure.
Just like the DLP security policy exceptions, this figure must be kept at a minimum in order to avoid incidents of the breach.
In conclusion
In this day and age, the implementation of a Data Loss Prevention solution is a necessary step in keeping your company’s data safe and under complete control. In addition, there are numerous benefits of data protection controls that got your business.
With the dangers of data loss and breaches growing, a fine-tuned data loss prevention policy is one of the foolproof mechanisms that help you to avoid sustaining financial and reputational damages from intentional malicious threats, system malfunctions, and unintentional human errors. Thus, you need to adopt data loss prevention best practices from this article.
Read also:
What is encrypted messaging apps like Wire and Signal?
Do you want to protect your data?
Write to us
