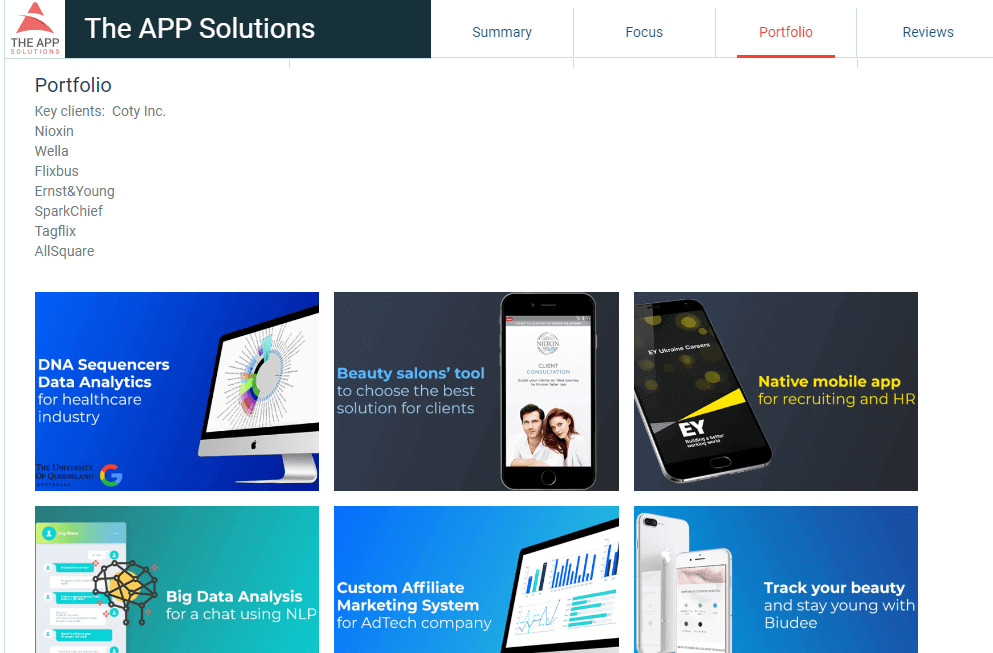
- Benefits of Artificial Intelligence in supply chain management
- AI and Machine Learning in Supply Chain: Best Applications
- Data-driven demand forecasting
- Visual recognition for automated quality control
- AI for automated warehouse management
- Real-time cargo monitoring
- Tips to integrate AI in logistics and supply chain with The APP Solutions
- Why adopt AI and machine learning in supply chain management
As a supply chain owner or C-level executive, you struggle to reduce inventory imbalances. At the same time, you want to achieve ultimate visibility and transparency across all departments. Unfortunately, the supply chain generates too much data, complicated to store and analyze. But there is a solution.
Fortunately, there are many AI and machine learning applications in supply chain management. The latest annual MHI Industry report shows 60% of supply chain businesses will invest in the adoption of AI. Thus, in the future, there will be more companies that use AI in supply chains.
In a previous article, we talked about AI in the logistics and transportation business. Now, we will highlight AI applications in the supply chain. At the end of this article, you’ll find tips for AI implementation, understandable even for a non-tech person.
Let’s take a quick look at the benefits you will get after implementing artificial intelligence in your supply chain.
Benefits of Artificial Intelligence in supply chain management
Intelligent technologies improve supply chain management. AI-powered software can analyze large amounts of data, define trends at a granular level, and react immediately. The benefits of AI in the supply chain listed below show more reasons why AI adoption matters for your supply chain business.
- Increased productivity is the main benefit of leveraging intelligent technologies. Over 60% of supply chain executives said AI could automate decision-making and improve supply chain efficiencies.
- The immediate reaction to changes is the main difference between humans and AI. AI software recognizes patterns and considers potential areas for improvements.
- Optimized warehouse operations are impossible without data analytics and machine learning. Smart algorithms can plan and predict product demand. Thus, you can assign vehicles and direct them to locations with the most considerable demand.
- Reduced operating costs are another benefit of AI integration. This technology optimizes every minute and mile in the supply chain. For instance, AI helped United Parcel Service (UPS) to optimize routes beforehand and save $50m.
AI and ML in the supply chain have created new performance standards for supply chain effectiveness. They also help businesses to run automated operations, analyze data, and serve clients. If you want to modernize your supply chain with AI, it is high time to get some ideas on how you can do that.
AI and Machine Learning in Supply Chain: Best Applications
From quality control to warehouse management, AI is applicable at all stages of product distribution. Below, we gathered the best AI use cases in supply chain and related technologies.
Data-driven demand forecasting
Most businesses use supply chain planning (SCP) or supply chain management (SCM) systems to balance supply and demand. But only a few stakeholders know that AI provides you with data-driven demand predictions. Such predictions are especially relevant for fresh food providers. These products are easily damaged and perishable and have a short shelf life.
As a result, most of the food waste occurs at the end of the supply chain during product distribution and consumption. Roughly one-third of the food produced around the globe gets lost or wasted every year, according to this United Nations report. For food supply chain owners, it means that they lost a vast amount of money.
Luckily, demand prediction is one of the most popular uses of artificial intelligence in operations and supply chain planning. For this purpose, you can use ready-made platforms like Demand Guru, by LLamasoft. The platform is forecasting demand in the supply chain using machine learning algorithms and identifying demand patterns.
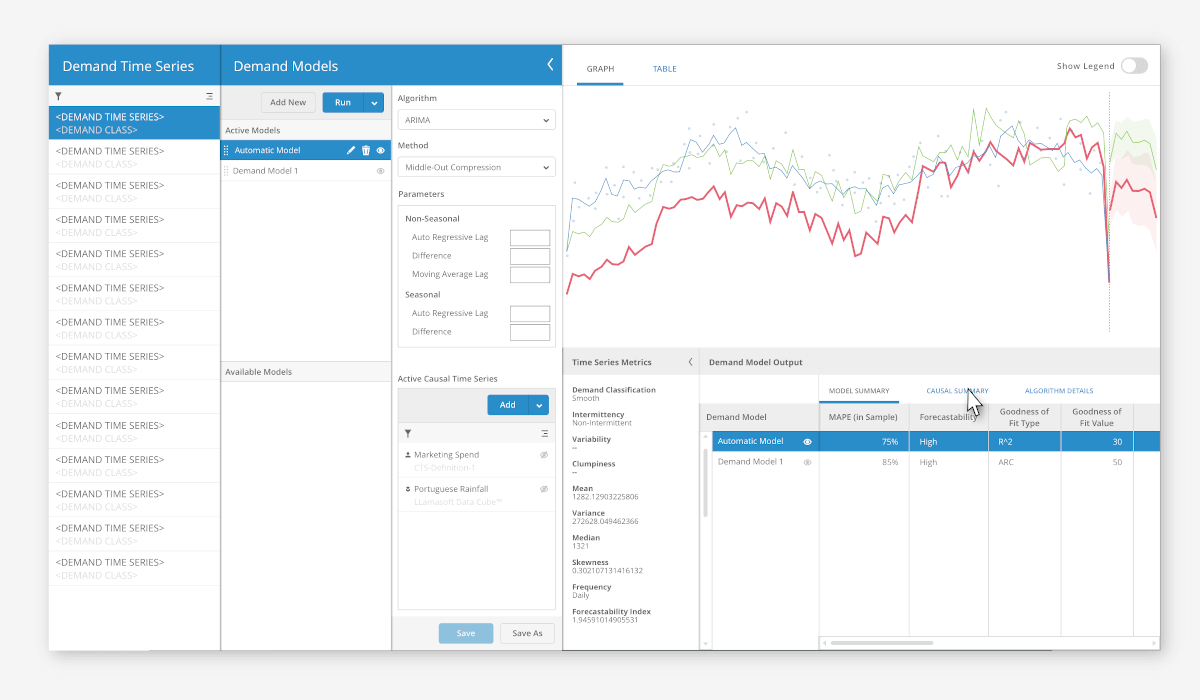
[Source]
Apart from long-term predictions, Demand Guru predicts the everyday demand for particular products. Moreover, this software can recognize the causes of increased demand and even create simulations of such situations. As a result, you receive more precise predictions generated by machine learning algorithms.
[Source]
Visual recognition for automated quality control
No one wants to buy damaged products. Thus, most supply chains have manual quality inspections to find damage during transit. This is where computer vision technology, one of machine learning in supply chain use cases, comes in handy. Computer vision can identify images and particular objects. As an example, Facebook uses computer vision to find existing users on photos and tag them.
For digitizing quality control, consider Fujitsu Advanced Image Recognition (F|AIR). This platform is a perfect solution for visual product inspection and defect detection. Thanks to this intelligent algorithm, the platform is more precise in object detection than other machine vision software.

[Source]
Once the platform identifies damaged goods, it will send you a PDF report, complete with defect images. F|AIR will help you to improve the consistency of quality inspection across your supply chain and reduce quality control costs up to 80%.
F|AIR works both on-premise and in the cloud to suit the existing supply chain ecosystem. You also can integrate F|AIR API into your system with help from a dedicated development team.
[Source]
AI for automated warehouse management
To use Artificial Intelligence in logistics and supply chain management, consider integrating automated robots. Such robots will streamline product picking, unloading pallets, and even packing items. Apart from saving operating costs, robots can provide you with data-based decision making.
Related reading:
BARCODE SCANNING APP FOR INVENTORY MANAGEMENT DIGITALIZATION
Each day your warehouse produces a massive amount of data. This may include inventory stock levels, order numbers, and shipping details. To get the most from this data using data analytics, think about doctors with machine learning capabilities. Such robots will identify patterns, predict out-of-stock items, orders, and even returns.
Ocado Technology is the online grocery retailer that nailed automated warehouse management. Ocado does not own any brick and mortar stores and receives orders only from their online store.

[Source]
To digitize its warehouse, Ocado developed most of its solutions with in-house development teams. Currently, the company’s main tech stack includes cloud computing, robotics, AI, and IoT. Ocado also put much effort into fraud detection using machine learning technologies. The company has built its custom route optimization platforms to always deliver fresh groceries.
Let’s see how Ocado’s automated warehouse management system works.
[Source]
- Ocado’s warehouse looks like a giant hive with a 3D grid structure inside where goods are stored.
- Ocado’s central system receives information about the products required.
- The system sends requests via 4G to robots that start collecting the required products from baskets.
- Artificial Intelligence controls all robots via an air traffic control system, so they can collect products without colliding.
- Once all products are collected, the order goes to pick stations, where robots or human employees assemble orders.
Currently, over 3500 robots operate in Ocado’s warehouse, which is 36 acres. Thanks to such automation, Ocado processes 220,000 orders a week.
Real-time cargo monitoring
All international supply chain owners want to increase transparency by tracking ocean freight in real-time—especially those who transport food and need to control the temperature in the transportation unit.
Related reading:
HOW TO CREATE A GPS APP FOR ANDROID AND IOS
To receive real-time cargo monitoring, consider integrating Arviem. This is a cargo monitoring platform, available for web and mobile, that tracks your cargo in the air, on land, and at sea. Moreover, it tracks the location, condition, and temperature of cargo during the journey of your products. Another advantage of Arviem’s is the intelligent ETA calculation. This algorithm will inform you about possible delays so that you can take proactive action.
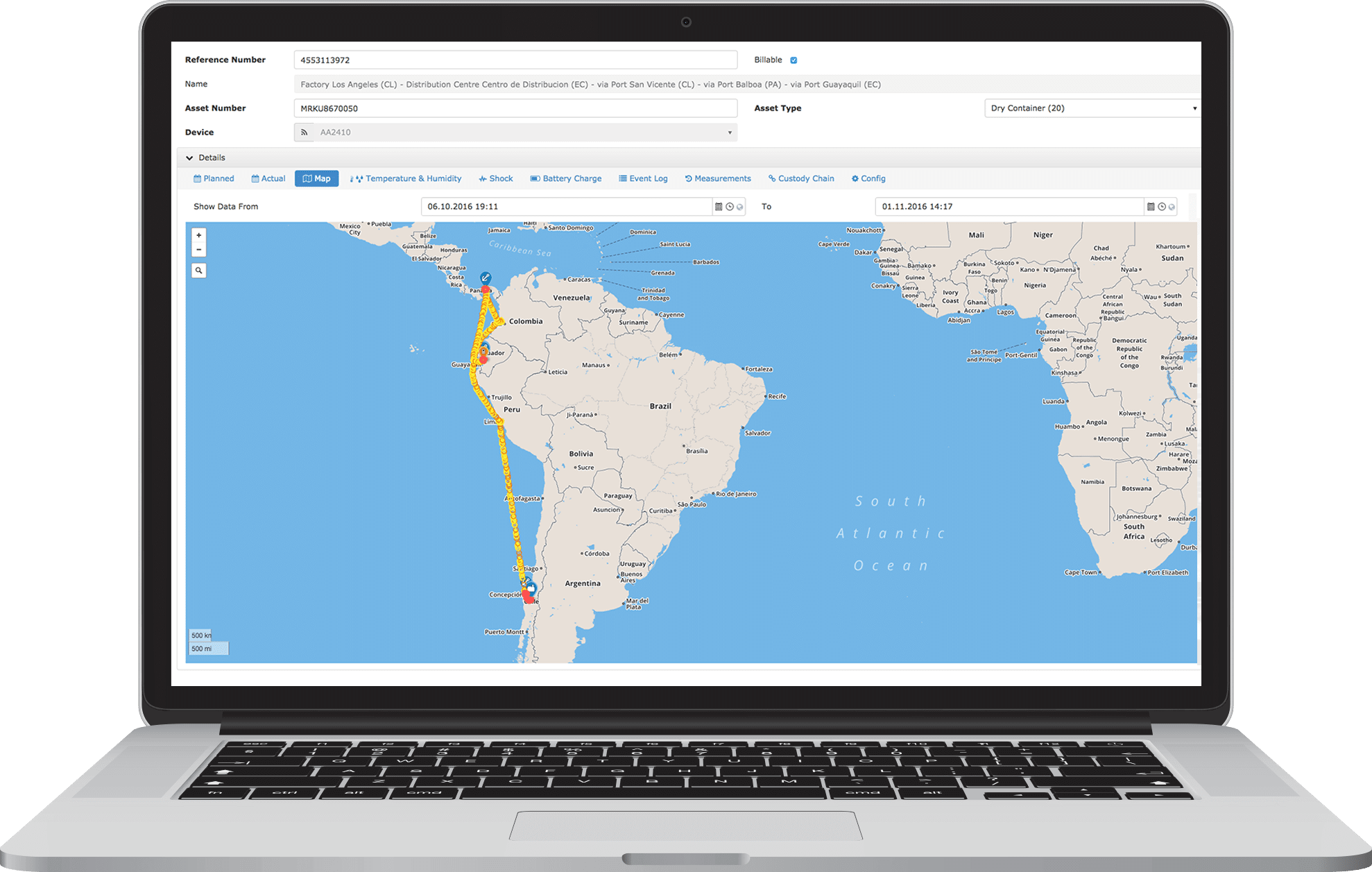
[Source]
The Arviem system consists of two main components:
- IoT devices that you attach to the cargo at the point of loading. These devices track humidity, temperature, light, and GPS location while the shipment is in transit. Then, IoT sensors send data to the analytics platform.
- The analytics platform receives information from devices and provides you with a quick picture of the cargo in transit. You also receive an in-depth analysis and route visualization. In this way, you can uncover inefficiencies and logistics blind spots and improve them.
Considering Developing a Logistics Software?
Download Free EbookNow, let’s find out what you need to adopt AI and ML in the supply chain and launch your project.
Tips to integrate AI in logistics and supply chain with The APP Solutions
Let’s see how you can adopt AI and machine learning in your supply chain.
Tip #1 See the bigger picture
Our clients often quote us for AI algorithm development. But, most of them do not know exactly which problems they need to solve.
Before integrating Artificial Intelligence because it’s hype tech, take a look around. Identify the problems you need to solve or areas to improve. If you are in doubt, consider hiring Data scientists. They will gather your business data, analyze it, and advice areas to integrate AI.
Tip #2 Choose wisely
With a clear understanding of your problems, start searching AI developers. During the search, pay attention to the developer’s certifications and Clutch profile with reviews from previous clients. Remember to ask about their experience with ML platforms, such as TensorFlow, IBM, and others. You may also want to take a look at their ML-specific case studies.
Tip #3 Develop a proof of concept
Your ML developers need to determine the right data sources for your AI project. They also need to decide the data types to ensure the supply chain has enough information. Next, you and your team will start creating a project scope for proof of concept. In this way, your development team will concentrate on the most critical aspects of your supply chain. As a result, you will receive the right type of AI that drives meaningful outcomes and uncover a clear path for further improvements.
Why adopt AI and machine learning in supply chain management
The adoption of AI into the supply chain is the main priority for 55% of supply chain stakeholders. Such technology helps to increase product quality, improve transparency, and make your business more predictable. Thus, to keep up with the trends in your industry, you also need to integrate AI and machine learning into the retail supply chain.
We hope this article has inspired you to further modernize your supply chain. If you have any questions on AI and ML in the supply chain or have enough courage to develop such software from scratch, write to us, and we will help.
What our clients say